Azure Key Vault is a service provided by Azure. It offers a secure storage solution for keys, secrets (passwords and other sensitive information you may want to hide), and certificates. AKV will encrypt keys and secrets for your applications. Azure handles all of the infrastructure which means you will not be responsible for provisioning, having to configure, or patching like you would with similar key management software. AKV also offers improved performance and less latency than on-premise solutions.
Let's figure out how we can add a secret to our Azure Key Vault and retrieve them in an application such as an Azure function. Creating and retrieving keys or certificates can be accomplished in a similar fashion. I will refrain from providing too much detail about creating the resources.
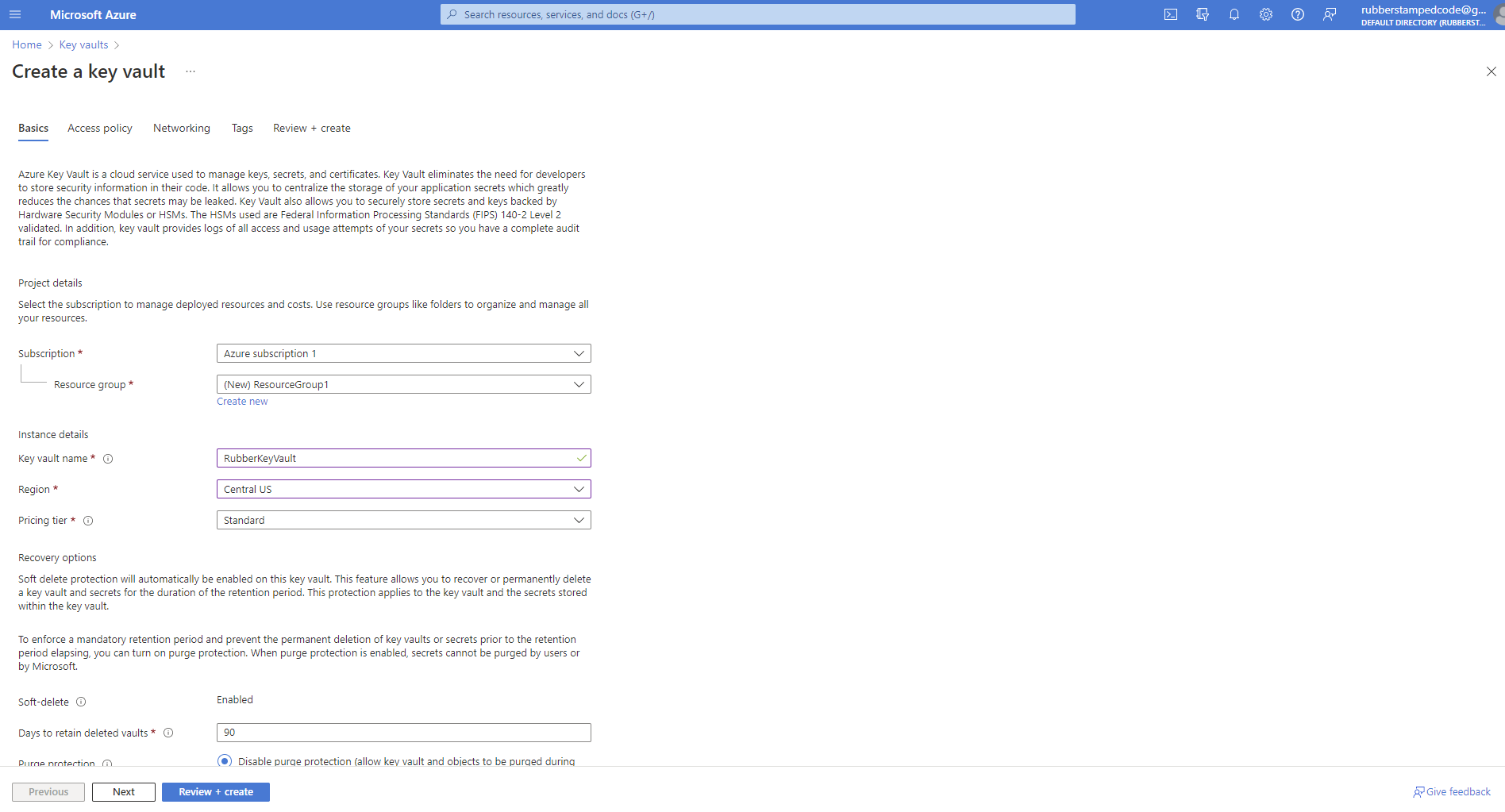
1. Create an Azure Key Vault storage resource
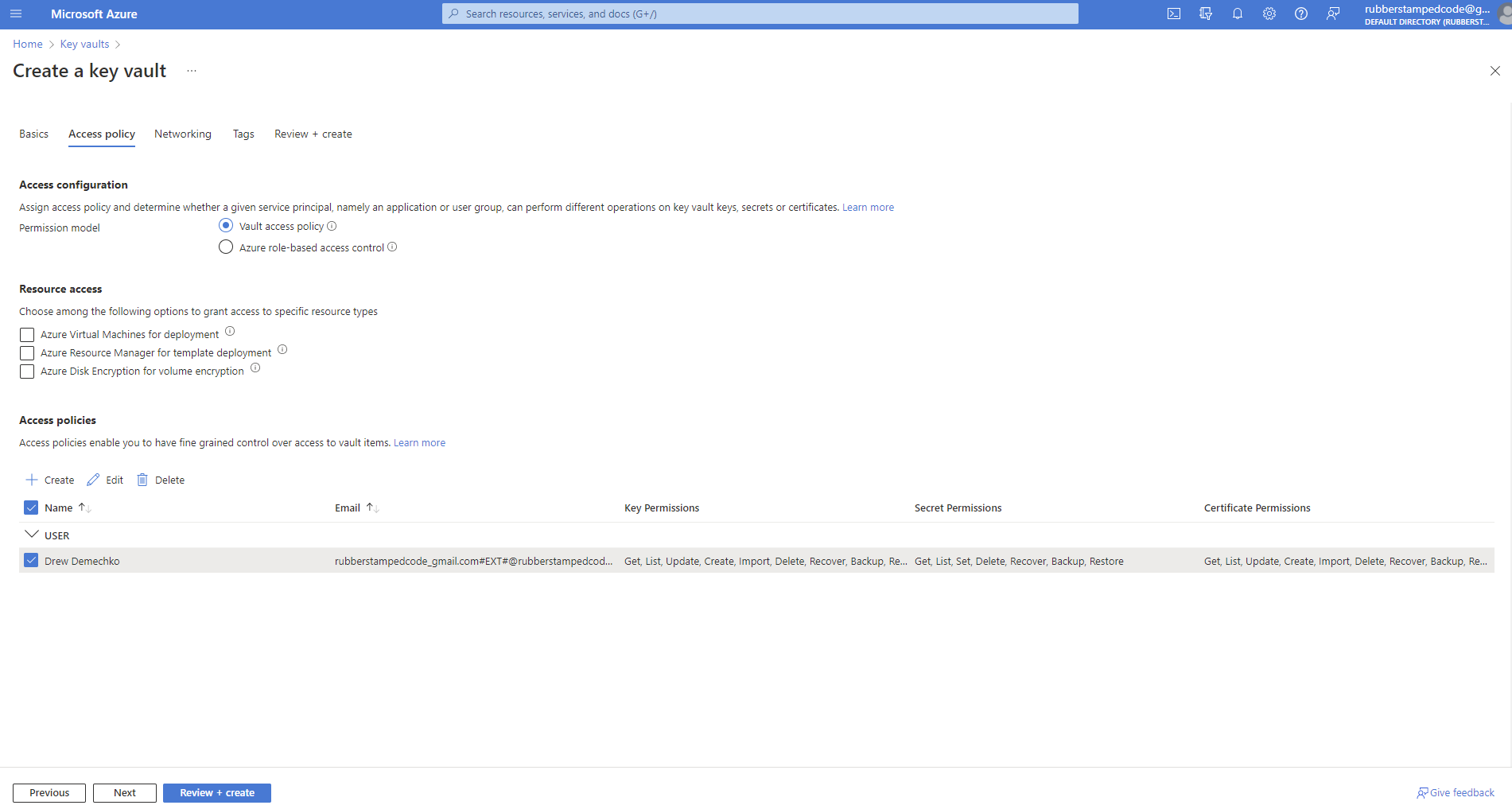
The important part here is to have the vault access policy set to on and to give your Azure account access.
2. Add a secret to the vault
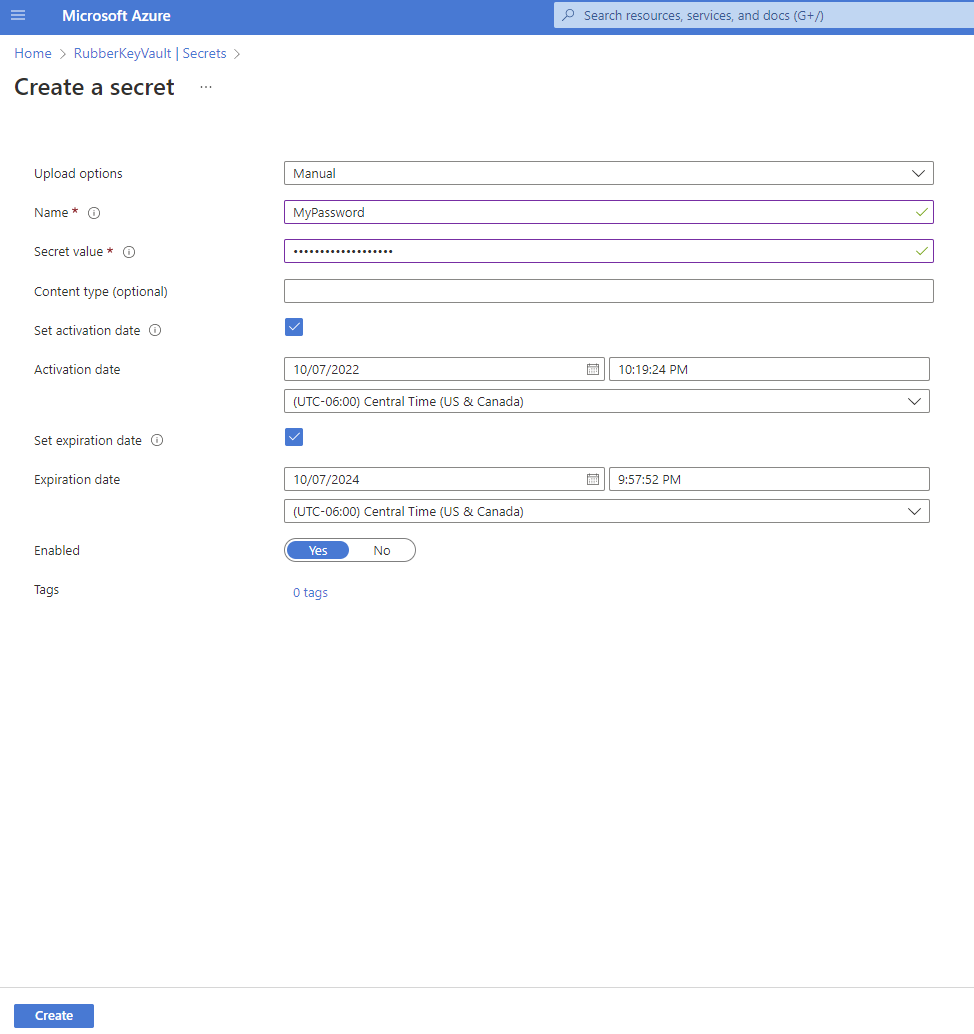
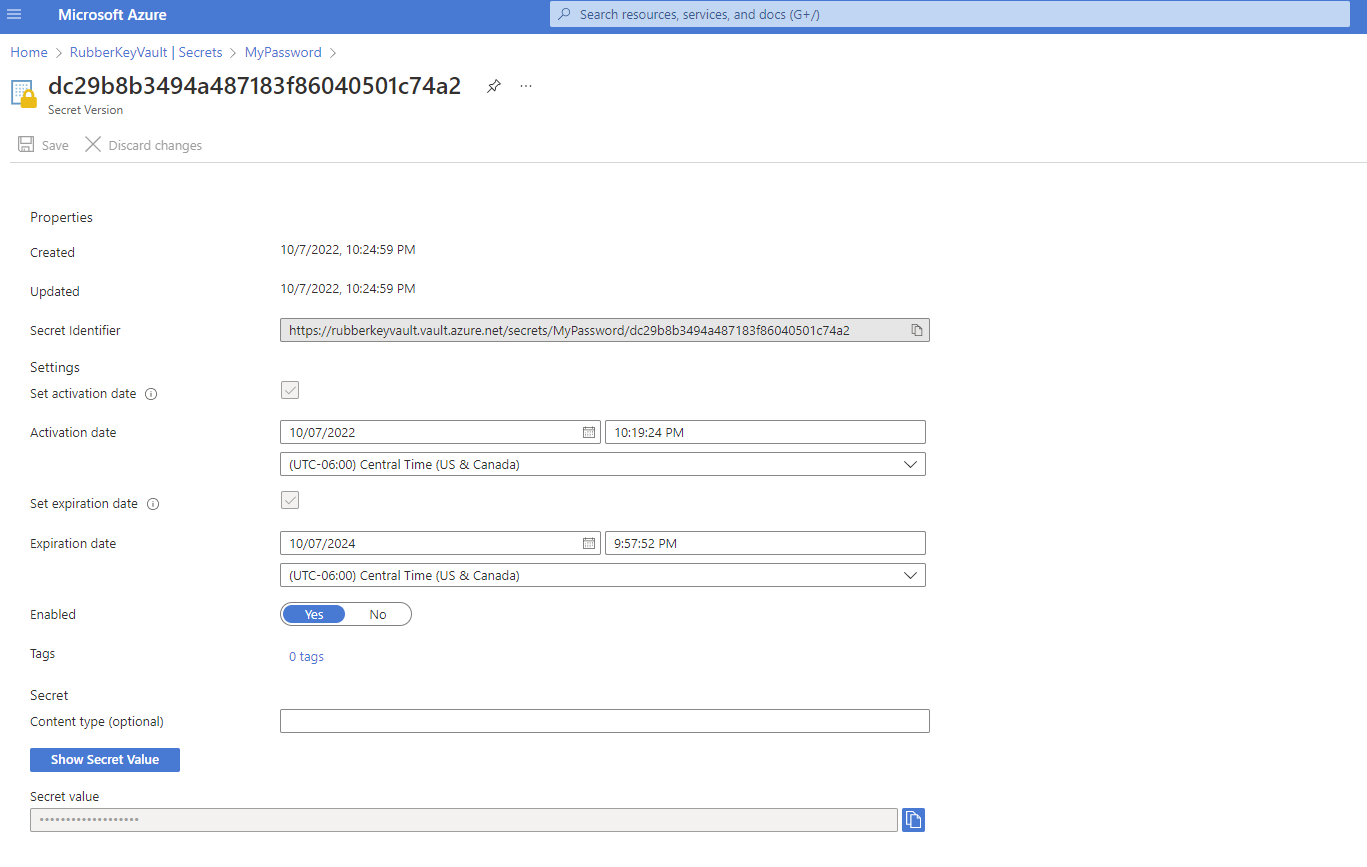
AKV gives you control to set activation and expiration dates and even let's you enable or disable them for whatever reason you may need to in the future.
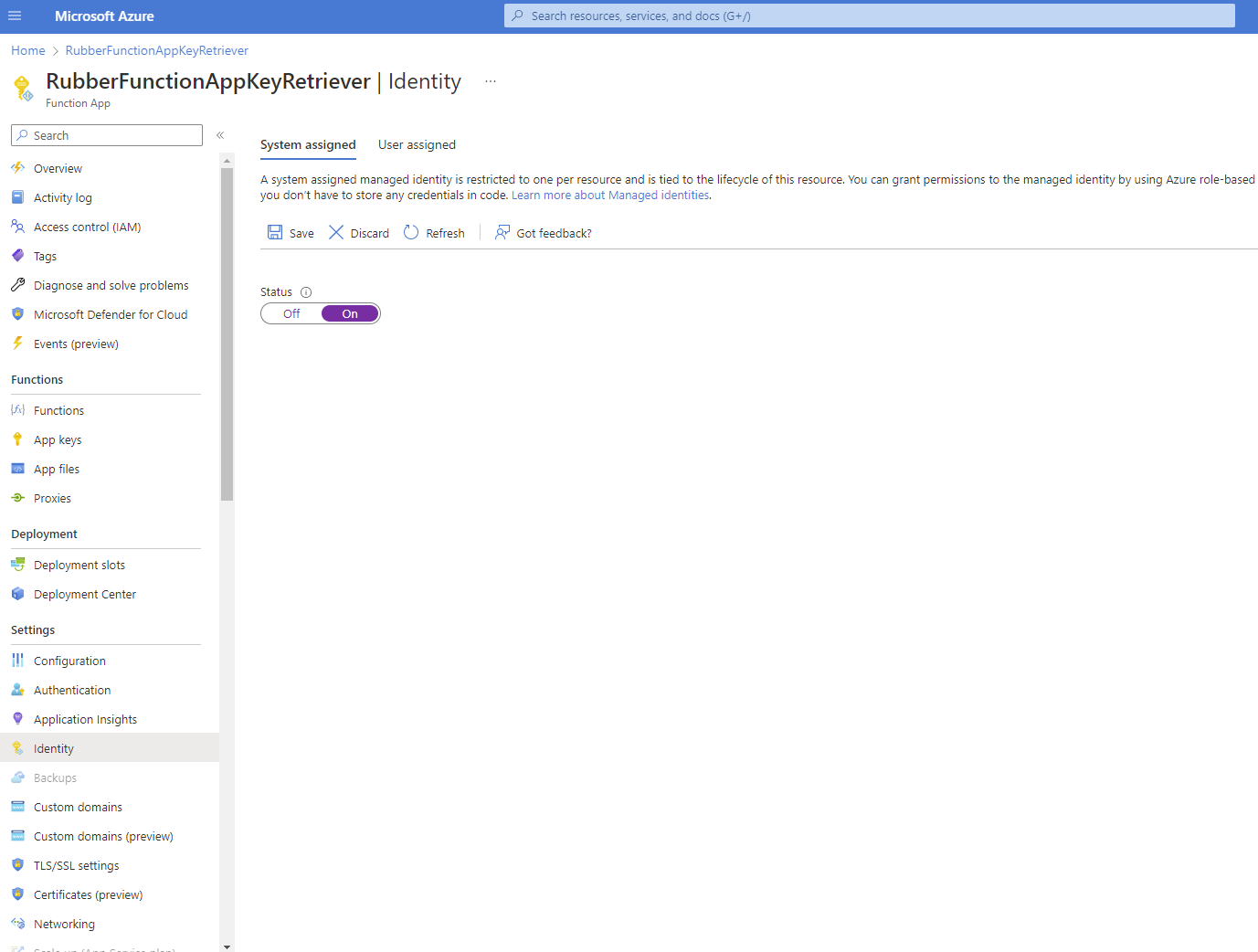
3. Turn on system identity for the resource that will be reading secrets from the key vault. This will give your resource a managed identity.
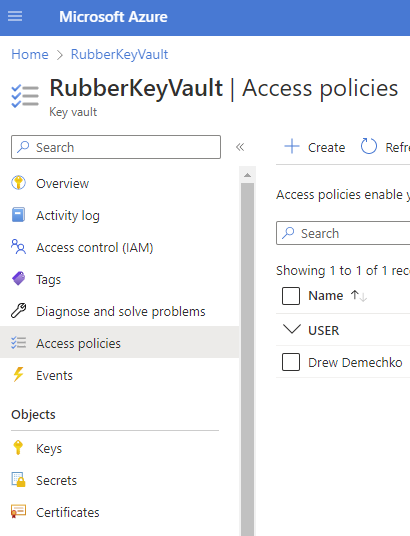
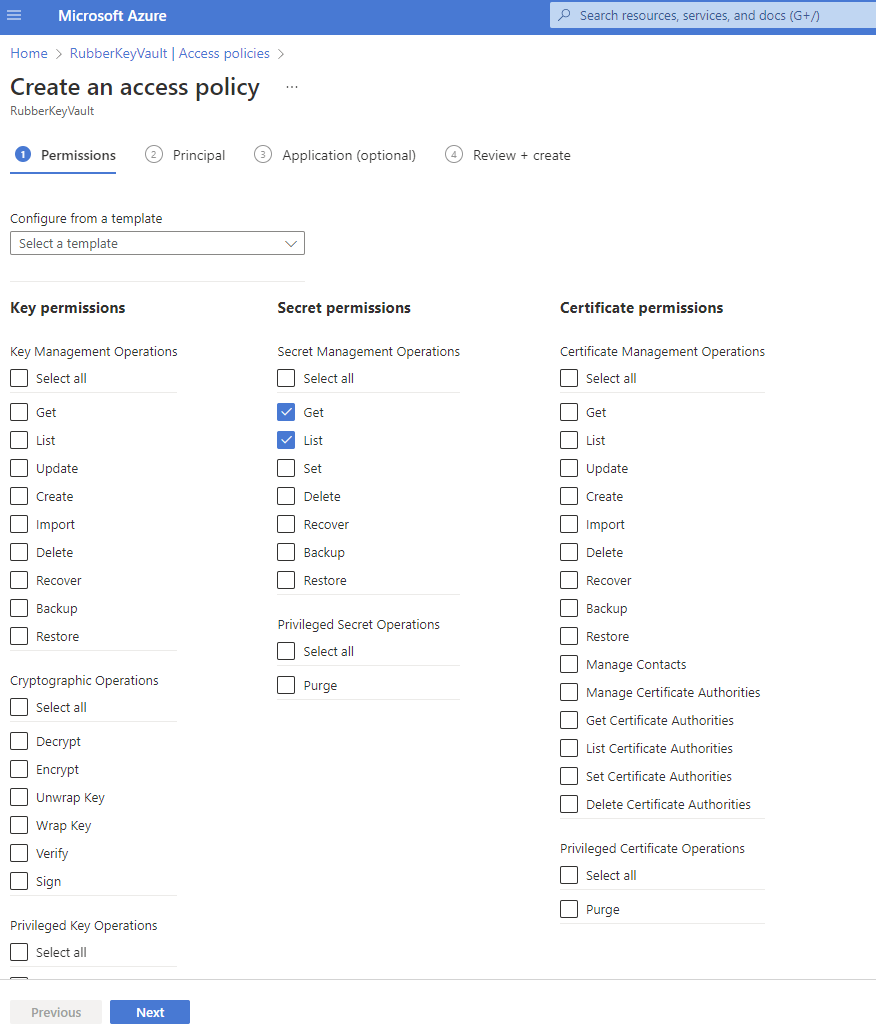
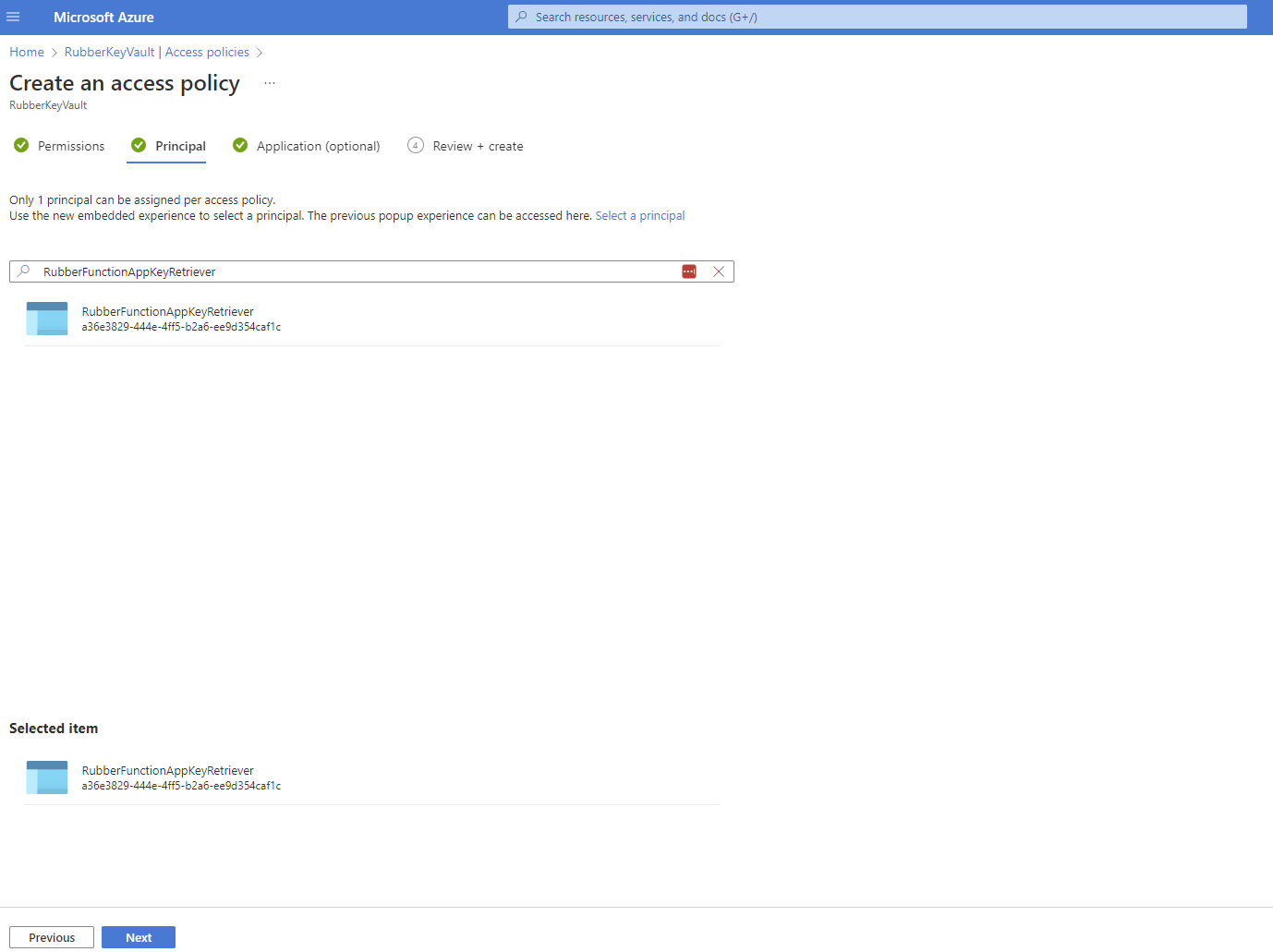
4. Grant the resource access to the key vault. From here you will be able to give specific permissions to managed identities. We will create an access policy to read secrets and assign the managed identity for the resource as the principal.
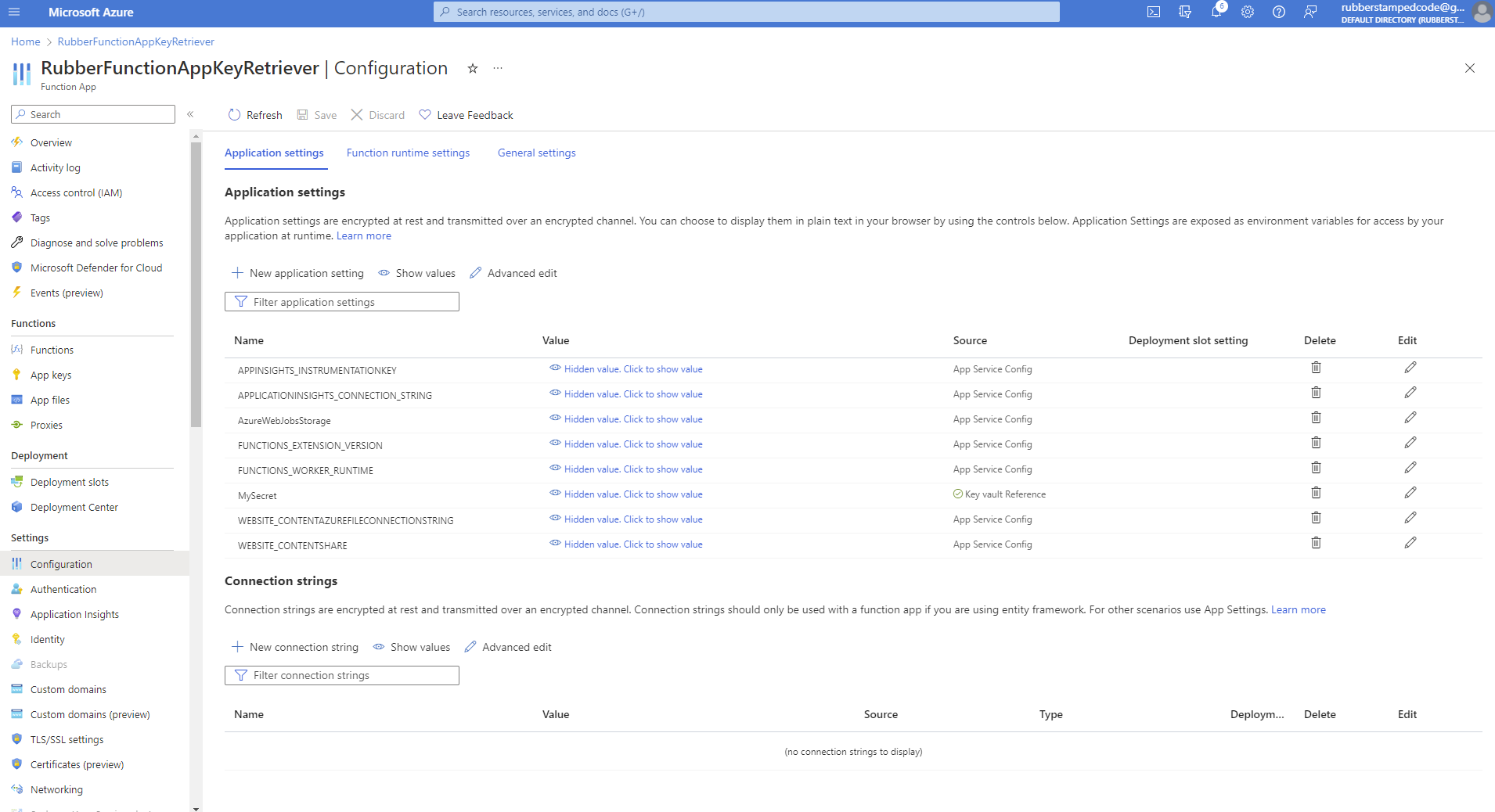
5. Add a configuration variable that will point to the secret we created.
@Microsoft.KeyVault(SecretUri={secret identifier})
You can always target the most recent version by ignoring the version which is dc29b8b3494a487183f86040501c74a2 in this example.
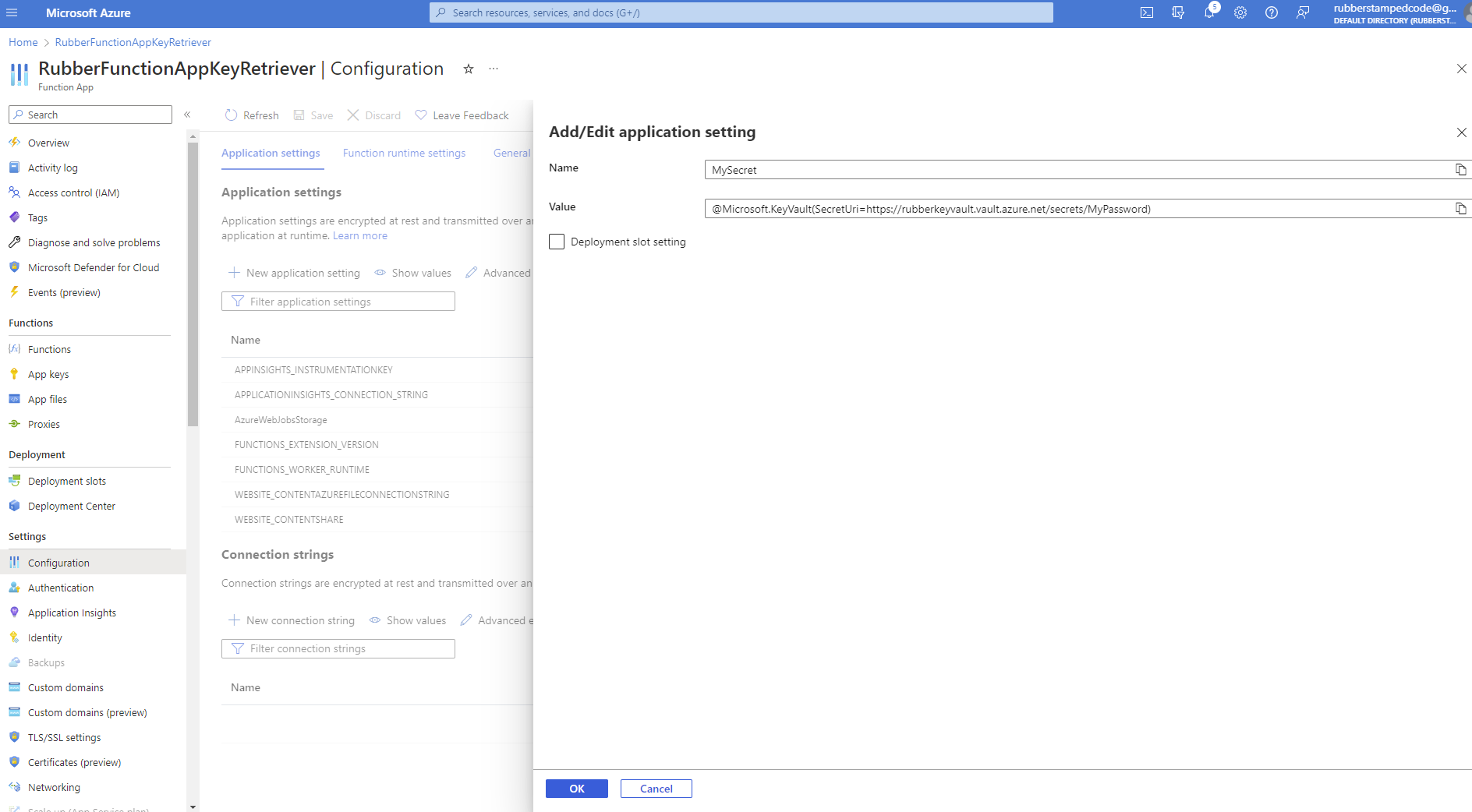
You can do a quick verification by refreshing your application settings and seeing if the source is key vault reference and shows a green checkmark.